What We Know So Far
StreamNetworks is actively reaching out to it’s customers regarding their recent security breach according to their post on X.
The company reports that the breach occurred from a 3rd party vendor they no longer do business with. While it may be simple to think that once you terminate a contract with a vendor you are done with them, the truth is often wildly different.
The threat actor (who calls themself “Victim”) alleged to have stolen some 210,000 customer records containing full names, addresses, phone numbers, and other information. A sample of the data was leaked to prove legitimacy.
“Victim” said they gained access via malware targeting a user at the third party vendor (which had not been used for about 1 year).
Details are still coming out and StreamEvents appears to be transparent with their findings.
So how could a Zero Trust Implementation have helped prevent this data breach? Let’s find out.
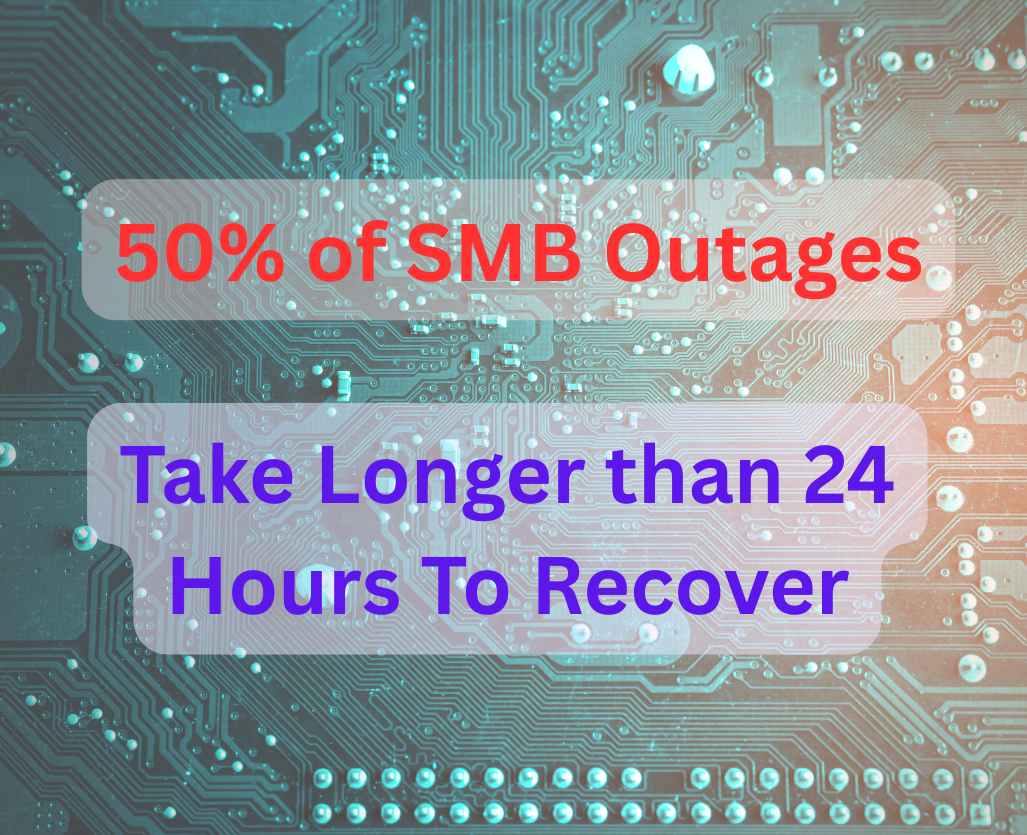
I’d put a serious amount of money down that StreamEvents has many security tools, malware detection software, and more all helping them manage today’s cyber threats. But for all the tools money can buy, it does no good without a solid strategy and a mindset for their business.
Security Sanctum: Third Party Vendor
In a proper Zero Trust security implementation, the third party vendor would have been identified as a Sanctum. Since we don’t know who the third party is, let’s call is Acme Services. That defines our protect surface as Acme Services Sanctum where we define how we secure communications, data access, policy and the like.
Since the Acme Services Sanctum contains external users who require access, we need to understand the data usage from StreamNetwork’s businesses & legal perspective. We’ll assume the business justification is there but we need to focus on what happens when the business justification goes away.
Legal teams should have (and perhaps did) dictate what happens to StreamNetworks data after the contract is terminated or ended as well as who is legally & financially responsible for data breaches or leaks.
Data Handling
Another aspect is who decides who has access to StreamNetwork’s data? Do justifications & requests flow through StreamNetworks or does Acme Services decide internally?
Having this data access (as well as data flow & usage) well defined may have prevented the breach all together!
Wrapping Things Up
Notice in our entire write-up we have not discussed a single tool or piece of software? This is because a Zero Trust Security implementation must be focused on the business, how data is accessed, how it is used, and defining responsibility. Software and tools help us automate and enforce a Zero Trust strategy, not define one.
Ready to start down your own Zero Trust implementation journey? Let us be your guide!